- Why INBOX
Why INBOX?
About us
We want to tell you a story
Why customers love us
Customer reviews
Find out why our customers love using INBOX
- Platform
Features
Email Marketing
Grow your audience
Automation
Send targeted emails automatically
Newsletter Design
Drag & Drop email editor
Personalization & Segmentation
Send personalized emails
Landing Pages
Create beautiful pages
Sign Up Forms
Grow your email list
A/B Testing
Send emails with A/B testing
Auto Resend Campaign
Automatically send a second campaign
Transactional Emails
Send emails with API or SMTP
Email Verification
Clean your email list
INBOX Cold
Reach new customers
INBOX Touch
The future of networking
- Partner
- Pricing
- Resources
Learn
Blog
Read best practices and stay up-to-date with news.
Youtube Videos
Email marketing academy
Customer Reviews
What says our clients
Company
Contact Us
Write us
Careers
Join the INBOX team
Integrations
Connect INBOX with popular apps
For Developers
Check our API documentation
Personal Data Breach Procedure
Personal Data Breach Procedure
- Background
UseINBOX’s committed to a policy of protecting individuals’ right to privacy in accordance with the General Data Protection Regulation ((EU) 2016/679) (the GDPR) and the Data Protection Act 2018 (the DPA). This document sets out the guidance and procedure for personal data breach incidents at UseINBOX and must be read in conjunction with UseINBOX’s Data Protection Policy.
UseINBOX is required to take appropriate measures against accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, personal data. The GDPR requires UseINBOX to report all personal data breaches (except those which are “unlikely to result in a risk to the rights and freedoms of natural persons”) to the Information Commissioner’s Office within 72 hours of becoming aware of the breach, and to maintain a log of all breaches. Failure to comply with the GDPR can lead to enforcement actions, including fines of up to €20 million or, if higher, 4% of an organization’s annual turnover.
Although, UseINBOX performs periodic audits of its privacy and data protection program, it is crucial that UseINBOX has a robust breach detection, investigation and internal reporting procedure in place. This procedure applies to UseINBOX staff and third party agents who process data for or on behalf of UseINBOX and it must be complied with in the event of a data security breach.
- What is a personal data breach?
The GDPR defines a personal data breach as a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to, personal data transmitted, stored or otherwise processed.
Personal data is any information relating to an identified or identifiable individual; an identifiable individual is one who can be identified, directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, an online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that individual.
A personal data breach can happen for a number of reasons. In general terms, a breach will occur whenever any personal data is lost, destroyed, corrupted or disclosed. Data breaches can fall into three categories:
- “Confidentiality breach” – where there is an unauthorised or accidental disclosure of, or access to, personal data.
- “Integrity breach” – where there is an unauthorised or accidental alteration of personal data.
- “Availability breach” – where there is an accidental or unauthorised loss of access to, or destruction of, personal data
Examples of data breaches include:
- Loss or theft of data or equipment on which data is stored (e.g. loss or theft of a computer, portable device, such as a laptop or data stick)
- Unauthorised access to, use, or alteration of personal data
- Deliberate or accidental action (or inaction)
- Loss of availability of personal data (e.g. encrypted by ransomware, or accidentally lost or destroyed) or through equipment failure (e.g. data cannot be accessed and is not backed up)
- Human error (e.g. sending data to the wrong recipient or accidentally deleting it)
- ‘Phishing’ offences where information is obtained by a third party through deception.
- What should I do when a breach occurs?
Any individual who accesses, uses or manages UseINBOX’s information is responsible for reporting a personal data breach and information security incidents immediately to the support team (at [email protected]) and Head of the relevant team of UseINBOX (at [email protected]). If the breach occurs or is discovered outside normal working hours, it must be reported as soon as is practicable.
If you know or suspect a personal data breach has occurred you should IMMEDIATELY:
- complete a data breach report form, as set out in Appendix 1.
- email or deliver the completed form to [email protected] and [email protected].
- On discovery of a breach
If the breach is a continuing breach, steps must be taken immediately to minimise the effect of the breach, e.g. to shut down a system or alert relevant staff.
Following receipt of a report of a suspected breach the Head of the relevant team and support team will confirm whether a breach has occurred and assess the risks associated with it. They will ask the person reporting the breach to provide full and accurate details of the incident, when the breach occurred (dates and times), if the data relates to people, the nature of the information, and how many individuals are involved.
An initial evaluation will be made by the support team and Head of the relevant team in liaison with relevant staff to establish the severity of the breach and who will take the lead investigating the breach (this will depend on the nature of the breach in some cases it could be the Head of the relevant team or another person
).
The evaluation of the breach will include an assessment of:
- the type of data involved
- its sensitivity
- the protections which are in place (e.g. encryptions)
- what has happened to the data (e.g. has it been lost or stolen)
- whether the data could be put to any illegal or inappropriate use
- who the individuals are, number of individuals involved and the potential effects on those data subject(s)
- whether there are wider consequences to the breach
The person leading the investigation will contact the Head of the relevant team to explain:
- the nature of the breach
- an indication of the seriousness of the breach
- any action UseINBOX or Service must take immediately
- to contain the breach and
- to become compliant with the GDPR/DPA and/or
- to prevent a similar situation from arising in the future.
The support team and Head of the relevant team will continue to monitor the situation to ensure that the department responsible for the breach completes any required actions as soon as possible.
- Managing the consequences of a breach
Depending on the seriousness of the breach, Head of the relevant team may advise on what further steps should be taken, which may include:
- informing the support team
- informing the Relevant Government Entity (this is mandatory where there is a risk to people’s rights and freedoms)
- informing the Director of Marketing and External Relations (if there is not a Director, the support team carries this task) if there is potential for press interest
- informing the data subjects affected by the breach.
When informing the data subjects, UseINBOX takes action by three essential elements:
- Time: The sooner UseINBOX can alert customers, the sooner they can take steps to protect themselves from any possible harm.
- Information: UseINBOX will try to give customers as much information as possible about the nature and extent of the breach.
- Thoroughness: UseINBOX will use multiple communication channels to make sure that all affected parties are notified of the breach
- Record keeping
UseINBOX maintains a Personal Data Breach Register to record details of all breaches. This record is maintained by the DPO.
- Preventing a repetition of a breach
After completing the procedures set out above, the DPO will evaluate the breach and the effectiveness of UseINBOX’s response to it. The DPO will consider any changes that may be required to be made to UseINBOX policies and procedures to prevent a breach from recurring.
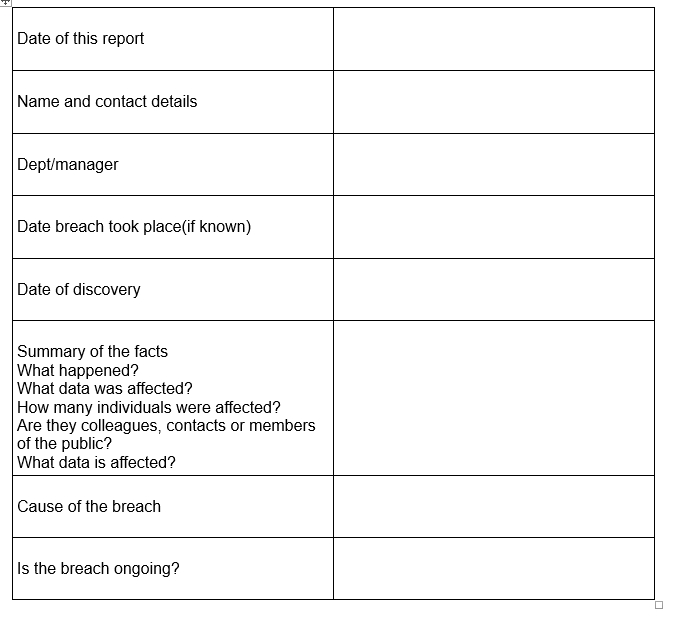
Appendix 1:
Personal data breach report form
If you know or suspect a personal data breach has occurred, please:
- complete this form, and
email or deliver it to [email protected] and [email protected] , ensuring you mark your email or the form as urgent